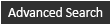
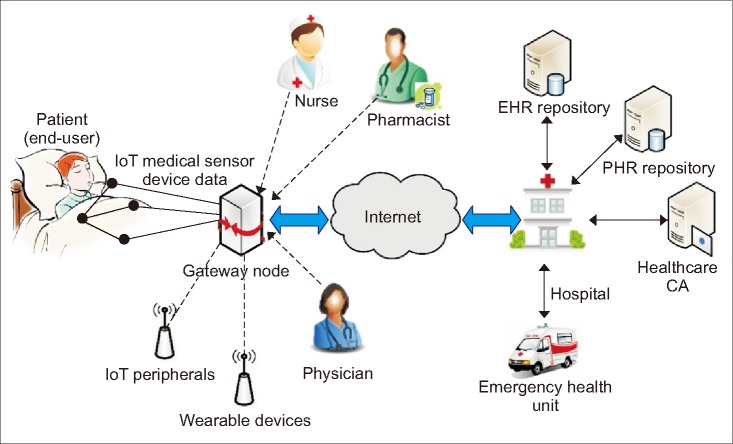
I. Introduction
II. Methods
1. Privacy-Enhancing Trust Levels
2. Context-Aware Management
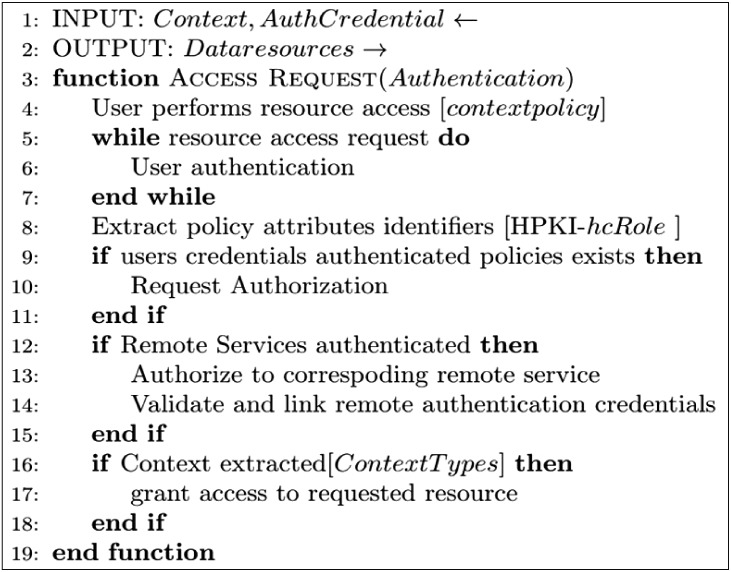
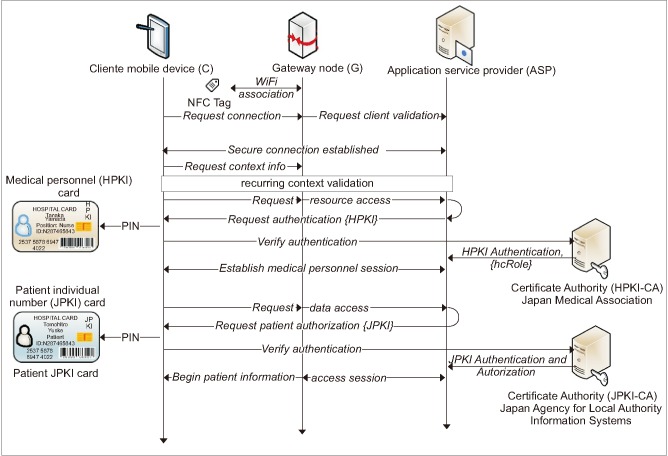
· Resource access request (1): A user (U) sends an access request based on context policy to authenticate to the service provider. If the user can meet the context policy requirements, then he or she can obtain a session from the session manager.
· Attribute and credential authentication (2)–(3): Otherwise, user attributes need to be authenticated and validated with the service provider access control as described later regarding the general authentication flow (see Section III-3). The system requests user credential verification based on the privacy-enhancing trust levels, in this case using the PKI card. Policy-enforcement module definitions are based on the hcRole coded into the HPKI cardholder's policy settings. The remote authentication service issues authenticated attribute credentials based on the hcRole and authorization from patient credentials.
· Assigning client sessions (4): The access manager (AM) maintains each session by assigning a temporary client session token. It assign tokens to the client CM for each user session-based access rights until ended by users or the policy-enforcement module.
· Context processing (5)–(6): It enforces policies based on information supplied by the context provider module, which uses metrics to establish the device's context types. Context collection is determined by the access policy. Context type may vary depending on its source, from a verified user's device context providers. The collected context is time stamped and digitally signed in to identify the context source.
· Context validation (7): The gateway node confirms and validates pre-defined context and runtime contextual information gathered from the user's smartphone. The context verifier (CV) accumulates all the contextual data to confirm whether the context satisfies the conditions of the policy. The CV sends an encoded time-stamp and challenge response to the context provider (CP) after validation. Thus, engineers examining the system security requirements can appropriately decide which context types will be used to define access.
· Policy validation (8): The policy verifier processes the predefined context policies provided by the policy decision point (PDP). The context data filter characterizes a policy enforcement point (PEP). It evaluates context data from the CP against the compiled policy rules, and the calls to request services are executed as user actions. Actions may include downloading files, updating healthcare information, and accessing limited data resources from other care providers. Context-aware policies are applied at user-end points of the client CM. These policies are maintained for every active user session to enable or reject access for a user to specific healthcare information resources. Further steps involve ordinary authorization, which is described in Section III-3 in relation to trust-level credential authentication and authorization. The corresponding context policy is based on Figure 5.